[et_pb_section fb_built=”1″ prev_background_color=”#ffffff” admin_label=”Financing” _builder_version=”4.16″ use_background_color_gradient=”on” background_color_gradient_stops=”rgba(27,31,37,0.3) 0%|#1b1f25 100%” background_color_gradient_overlays_image=”on” background_color_gradient_start=”rgba(27,31,37,0.3)” background_color_gradient_end=”#1b1f25″ background_image=”https://itcstpete.com/wp-content/uploads/2022/02/penetration-testing-image-1.jpg” vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_padding=”250px||0px||false|false” top_divider_style=”arrow” top_divider_height_tablet=”” top_divider_height_phone=”50px” top_divider_height_last_edited=”on|phone” z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][et_pb_row module_class=” et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth et_pb_row_fullwidth” _builder_version=”4.16″ width=”89%” width_tablet=”80%” width_phone=”” width_last_edited=”on|desktop” max_width=”89%” max_width_tablet=”80%” max_width_phone=”” max_width_last_edited=”on|desktop” custom_margin=”|||” custom_padding=”0|0px|0px|0px|false|false” make_fullwidth=”on” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_text admin_label=”Ransomware Attacks” _builder_version=”4.17.3″ header_font=”Teko|500|||||||” header_text_color=”#ffffff” header_font_size=”9vw” header_line_height=”0.7em” header_2_font=”Teko|500||on|||||” header_2_text_color=”#ffffff” header_2_font_size=”9vw” header_2_line_height=”1.2em” vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ text_orientation=”center” animation_style=”zoom” animation_delay=”100ms” animation_intensity_zoom=”20%” header_font_size_tablet=”” header_font_size_phone=”” header_font_size_last_edited=”on|phone” header_line_height_tablet=”” header_line_height_phone=”1.2em” header_line_height_last_edited=”on|phone” z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Ransomware Attacks
[/et_pb_text][et_pb_text admin_label=”Title” _builder_version=”4.17.3″ text_font=”Lato||||||||” text_font_size=”28px” header_2_font=”Teko||||||||” header_2_text_color=”#ffffff” header_2_font_size=”35px” header_3_font=”Teko||||||||” header_3_font_size=”40px” header_3_line_height=”1.2em” vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_margin=”||15px|” z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Stay Protected From Unwanted Threats
[/et_pb_text][et_pb_text _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
There are many ways to stay proactive and stay protected so you don’t get hit with a ransomware attack.
We will asses your business needs and provide you with our Expert-Recommended solutions to keep you protected.
[/et_pb_text][/et_pb_column][/et_pb_row][et_pb_row _builder_version=”4.16″ custom_margin=”|||” custom_padding=”||0px|” locked=”off” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_button button_url=”https://itcstpete.com/contact/” button_text=”Contact An Expert” button_alignment=”center” _builder_version=”4.16″ custom_button=”on” button_text_size=”16px” button_bg_color=”#c10f1b” button_border_width=”8px” button_border_color=”#c10f1b” button_border_radius=”0px” button_letter_spacing=”4px” button_font=”Teko|700||on|||||” button_icon=”$||divi||400″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ background_layout=”dark” z_index_tablet=”0″ button_text_shadow_horizontal_length_tablet=”0px” button_text_shadow_vertical_length_tablet=”0px” button_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}” button_text_size__hover_enabled=”off” button_text_size__hover=”null” button_one_text_size__hover_enabled=”off” button_one_text_size__hover=”null” button_two_text_size__hover_enabled=”off” button_two_text_size__hover=”null” button_text_color__hover_enabled=”off” button_text_color__hover=”null” button_one_text_color__hover_enabled=”off” button_one_text_color__hover=”null” button_two_text_color__hover_enabled=”off” button_two_text_color__hover=”null” button_border_width__hover_enabled=”off” button_border_width__hover=”null” button_one_border_width__hover_enabled=”off” button_one_border_width__hover=”null” button_two_border_width__hover_enabled=”off” button_two_border_width__hover=”null” button_border_color__hover_enabled=”off” button_border_color__hover=”null” button_one_border_color__hover_enabled=”off” button_one_border_color__hover=”null” button_two_border_color__hover_enabled=”off” button_two_border_color__hover=”null” button_border_radius__hover_enabled=”off” button_border_radius__hover=”null” button_one_border_radius__hover_enabled=”off” button_one_border_radius__hover=”null” button_two_border_radius__hover_enabled=”off” button_two_border_radius__hover=”null” button_letter_spacing__hover_enabled=”off” button_letter_spacing__hover=”null” button_one_letter_spacing__hover_enabled=”off” button_one_letter_spacing__hover=”null” button_two_letter_spacing__hover_enabled=”off” button_two_letter_spacing__hover=”null” button_bg_color__hover_enabled=”off” button_bg_color__hover=”null” button_one_bg_color__hover_enabled=”off” button_one_bg_color__hover=”null” button_two_bg_color__hover_enabled=”off” button_two_bg_color__hover=”null”][/et_pb_button][/et_pb_column][/et_pb_row][/et_pb_section][et_pb_section fb_built=”1″ _builder_version=”4.16″ global_colors_info=”{}”][et_pb_row column_structure=”3_5,2_5″ _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][et_pb_column type=”3_5″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_text admin_label=”Title – MDR/EDR/ITCSecure” _builder_version=”4.17.1″ header_3_font=”Teko||||||||” header_3_font_size=”50px” header_3_line_height=”1.2em” vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_margin=”||15px|” hover_enabled=”0″ header_3_font_size_tablet=”” header_3_font_size_phone=”40px” header_3_font_size_last_edited=”on|desktop” z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}” sticky_enabled=”0″]
Do you want to learn more about EDR/MDR Solutions and Network Security?
Inquire about ITCSecure for our affordable multi-layered approach to Cybersecurity.
[/et_pb_text][et_pb_text _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Ransomware has quickly become the most well-known type of malware. Recent ransomware attacks have impacted businesses of all types – from a Hospital’s ability to provide crucial services, to crippled Public Services in cities, causing significant damage to various organizations and people’s personal information.
The number of ransomware attacks is on the rise in recent years. Some organizations reported an 800% increase in ransomware occurrences year over year. According to some estimates, annual cybersecurity costs now exceed $1 trillion – and that’s only the cost of the effects themselves and not associated downtime or business continuity expenses.
The damage caused by these malicious software attacks can be devastating – it may cost organizations millions of dollars to recover their data, or even more than $1 million if customer data is stolen or destroyed by malware or ransomware attacks. But there are also many ways your business could be harmed if you’re not careful; most importantly perhaps being legal penalties from negligence because you couldn’t prevent cyberattacks on your business’ systems and network.
Download the e-brochure for details about how we can help your organization mitigate its security threats and secure itself from becoming another victim of lucrative Ransomware.
[/et_pb_text][et_pb_image src=”https://itcstpete.com/wp-content/uploads/2022/05/Mitigate-the-Risk-of-Ransomware.png” url=”https://itcstpete.com/wp-content/uploads/2022/05/xdr-solutions-network-security-florida.pdf” url_new_window=”on” align=”center” _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ hover_enabled=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}” sticky_enabled=”0″][/et_pb_image][et_pb_image src=”https://itcstpete.com/wp-content/uploads/2022/05/xdr-solutions-brochure.png” url=”https://itcstpete.com/wp-content/uploads/2024/04/ITCSecure-costs-Additional-Services.pdf” url_new_window=”on” align=”center” _builder_version=”4.17.1″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ hover_enabled=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}” sticky_enabled=”0″][/et_pb_image][/et_pb_column][et_pb_column type=”2_5″ _builder_version=”4.16″ background_color=”#e02b20″ background_pattern_horizontal_offset=”0px” background_pattern_vertical_offset=”0px” vertical_offset_tablet=”0″ vertical_offset_phone=”0″ horizontal_offset_tablet=”0″ horizontal_offset_phone=”0″ custom_padding=”40px|40px|40px|40px” custom_padding_tablet=”|||” custom_padding_phone=”|||” background_color_gradient_direction_tablet=”180deg” background_color_gradient_direction_phone=”180deg” background_color_gradient_stops_tablet=”#2b87da 0%|#29c4a9 100%” background_color_gradient_stops_phone=”#2b87da 0%|#29c4a9 100%” background_image_width_tablet=”auto” background_image_width_phone=”auto” background_image_height_tablet=”auto” background_image_height_phone=”auto” background_horizontal_offset_tablet=”0px” background_horizontal_offset_phone=”0px” background_vertical_offset_tablet=”0px” background_vertical_offset_phone=”0px” background_pattern_style_tablet=”polka-dots” background_pattern_style_phone=”polka-dots” background_pattern_width_tablet=”auto” background_pattern_width_phone=”auto” background_pattern_height_tablet=”auto” background_pattern_height_phone=”auto” background_pattern_horizontal_offset_tablet=”0px” background_pattern_horizontal_offset_phone=”0px” background_pattern_vertical_offset_tablet=”0px” background_pattern_vertical_offset_phone=”0px” background_mask_style_tablet=”layer-blob” background_mask_style_phone=”layer-blob” background_mask_width_tablet=”auto” background_mask_width_phone=”auto” background_mask_height_tablet=”auto” background_mask_height_phone=”auto” background_mask_horizontal_offset_tablet=”0px” background_mask_horizontal_offset_phone=”0px” background_mask_vertical_offset_tablet=”0px” background_mask_vertical_offset_phone=”0px” z_index_tablet=”2″ z_index_phone=”2″ filter_hue_rotate_tablet=”0deg” filter_hue_rotate_phone=”0deg” filter_saturate_tablet=”100%” filter_saturate_phone=”100%” filter_brightness_tablet=”100%” filter_brightness_phone=”100%” filter_contrast_tablet=”100%” filter_contrast_phone=”100%” filter_invert_tablet=”0%” filter_invert_phone=”0%” filter_sepia_tablet=”0%” filter_sepia_phone=”0%” filter_opacity_tablet=”100%” filter_opacity_phone=”100%” filter_blur_tablet=”0px” filter_blur_phone=”0px” animation_duration_tablet=”1000ms” animation_duration_phone=”1000ms” animation_delay_tablet=”0ms” animation_delay_phone=”0ms” animation_intensity_slide_tablet=”50%” animation_intensity_slide_phone=”50%” animation_intensity_zoom_tablet=”50%” animation_intensity_zoom_phone=”50%” animation_intensity_flip_tablet=”50%” animation_intensity_flip_phone=”50%” animation_intensity_fold_tablet=”50%” animation_intensity_fold_phone=”50%” animation_intensity_roll_tablet=”50%” animation_intensity_roll_phone=”50%” animation_starting_opacity_tablet=”0%” animation_starting_opacity_phone=”0%” hover_transition_duration_tablet=”300ms” hover_transition_duration_phone=”300ms” hover_transition_delay_tablet=”0ms” hover_transition_delay_phone=”0ms” box_shadow_horizontal_tablet=”0px” box_shadow_horizontal_phone=”0px” box_shadow_vertical_tablet=”0px” box_shadow_vertical_phone=”0px” box_shadow_blur_tablet=”40px” box_shadow_blur_phone=”40px” box_shadow_spread_tablet=”0px” box_shadow_spread_phone=”0px” disabled=”%91object HTMLInputElement%93″ global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_divider show_divider=”off” _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_divider][et_pb_contact_form captcha=”off” email=”info@itcstpete.com” title=”Schedule A Free Consultation” custom_message=”%%name%%||et_pb_line_break_holder||%%email%%||et_pb_line_break_holder||%%message%%” success_message=”Your message has been sent.” submit_button_text=”Send Message” module_id=”et_pb_contact_form_0″ _builder_version=”4.17.3″ form_field_background_color=”rgba(0,0,0,0.15)” form_field_text_color=”#ffffff” form_field_focus_background_color=”#ffffff” title_font=”Teko||||||||” title_text_color=”#ffffff” title_font_size=”40px” title_line_height=”1.2em” captcha_text_color=”#ffffff” form_field_font=”Lato||||||||” form_field_font_size=”16px” custom_button=”on” button_text_color=”#c10f1b” button_bg_color=”#ffffff” button_border_width=”8px” button_border_color=”#ffffff” button_border_radius=”0px” button_letter_spacing=”4px” button_font=”Teko|||on|||||” button_icon=”$||divi||400″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ title_text_shadow_horizontal_length_tablet=”0px” title_text_shadow_vertical_length_tablet=”0px” title_text_shadow_blur_strength_tablet=”1px” captcha_text_shadow_horizontal_length_tablet=”0px” captcha_text_shadow_vertical_length_tablet=”0px” captcha_text_shadow_blur_strength_tablet=”1px” form_field_text_shadow_horizontal_length_tablet=”0px” form_field_text_shadow_vertical_length_tablet=”0px” form_field_text_shadow_blur_strength_tablet=”1px” button_text_shadow_horizontal_length_tablet=”0px” button_text_shadow_vertical_length_tablet=”0px” button_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” box_shadow_horizontal_button_tablet=”0px” box_shadow_vertical_button_tablet=”0px” box_shadow_blur_button_tablet=”40px” box_shadow_spread_button_tablet=”0px” text_shadow_horizontal_length_tablet=”0px” text_shadow_vertical_length_tablet=”0px” text_shadow_blur_strength_tablet=”1px” form_background_color=”rgba(0,0,0,0.15)” global_colors_info=”{}”][et_pb_contact_field field_id=”Name” field_title=”Name” fullwidth_field=”on” _builder_version=”4.16″ global_colors_info=”{}” button_text_size__hover_enabled=”off” button_one_text_size__hover_enabled=”off” button_two_text_size__hover_enabled=”off” button_text_color__hover_enabled=”off” button_one_text_color__hover_enabled=”off” button_two_text_color__hover_enabled=”off” button_border_width__hover_enabled=”off” button_one_border_width__hover_enabled=”off” button_two_border_width__hover_enabled=”off” button_border_color__hover_enabled=”off” button_one_border_color__hover_enabled=”off” button_two_border_color__hover_enabled=”off” button_border_radius__hover_enabled=”off” button_one_border_radius__hover_enabled=”off” button_two_border_radius__hover_enabled=”off” button_letter_spacing__hover_enabled=”off” button_one_letter_spacing__hover_enabled=”off” button_two_letter_spacing__hover_enabled=”off” button_bg_color__hover_enabled=”off” button_one_bg_color__hover_enabled=”off” button_two_bg_color__hover_enabled=”off”][/et_pb_contact_field][et_pb_contact_field field_id=”Email” field_title=”Email Address” field_type=”email” fullwidth_field=”on” _builder_version=”4.16″ global_colors_info=”{}” button_text_size__hover_enabled=”off” button_one_text_size__hover_enabled=”off” button_two_text_size__hover_enabled=”off” button_text_color__hover_enabled=”off” button_one_text_color__hover_enabled=”off” button_two_text_color__hover_enabled=”off” button_border_width__hover_enabled=”off” button_one_border_width__hover_enabled=”off” button_two_border_width__hover_enabled=”off” button_border_color__hover_enabled=”off” button_one_border_color__hover_enabled=”off” button_two_border_color__hover_enabled=”off” button_border_radius__hover_enabled=”off” button_one_border_radius__hover_enabled=”off” button_two_border_radius__hover_enabled=”off” button_letter_spacing__hover_enabled=”off” button_one_letter_spacing__hover_enabled=”off” button_two_letter_spacing__hover_enabled=”off” button_bg_color__hover_enabled=”off” button_one_bg_color__hover_enabled=”off” button_two_bg_color__hover_enabled=”off”][/et_pb_contact_field][et_pb_contact_field field_id=”Message” field_title=”Message” field_type=”text” fullwidth_field=”on” _builder_version=”4.16″ global_colors_info=”{}” button_text_size__hover_enabled=”off” button_one_text_size__hover_enabled=”off” button_two_text_size__hover_enabled=”off” button_text_color__hover_enabled=”off” button_one_text_color__hover_enabled=”off” button_two_text_color__hover_enabled=”off” button_border_width__hover_enabled=”off” button_one_border_width__hover_enabled=”off” button_two_border_width__hover_enabled=”off” button_border_color__hover_enabled=”off” button_one_border_color__hover_enabled=”off” button_two_border_color__hover_enabled=”off” button_border_radius__hover_enabled=”off” button_one_border_radius__hover_enabled=”off” button_two_border_radius__hover_enabled=”off” button_letter_spacing__hover_enabled=”off” button_one_letter_spacing__hover_enabled=”off” button_two_letter_spacing__hover_enabled=”off” button_bg_color__hover_enabled=”off” button_one_bg_color__hover_enabled=”off” button_two_bg_color__hover_enabled=”off”][/et_pb_contact_field][/et_pb_contact_form][/et_pb_column][/et_pb_row][et_pb_row _builder_version=”4.16″ background_size=”initial” background_position=”top_left” background_repeat=”repeat” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_divider color=”#e02b20″ _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_divider][/et_pb_column][/et_pb_row][/et_pb_section][et_pb_section fb_built=”1″ admin_label=”Features” _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_padding=”|||” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][et_pb_row _builder_version=”4.16″ global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_text admin_label=”What is a Ransomware Attack?” _builder_version=”4.17.3″ header_3_font=”Teko||||||||” header_3_font_size=”40px” header_3_line_height=”1.2em” vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_margin=”||15px|” z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
What is a Ransomware Attack?
[/et_pb_text][et_pb_text _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]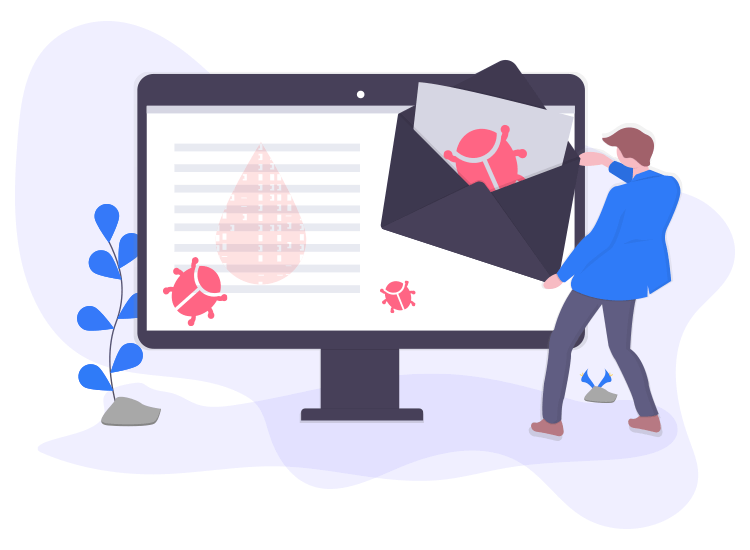
Ransomware attacks is a type of malicious software, or malware, that is designed to encrypt an organization’s or person’s files, and the only way to regain access them is through a decryption key which the bad actors hold until a ransom is paid. Ransomware attacks can cause costly disruptions to operations, and a loss of critical data and information. The ransom fee alone can cost millions of dollars.
Ransomware attacks has quickly become the most well-known type of malware. Recent ransomware attacks have impacted businesses of all types – from a Hospital’s ability to provide crucial services, to crippled Public Services in cities, causing significant damage to various organizations and people’s personal information. More information
[/et_pb_text][/et_pb_column][/et_pb_row][et_pb_row _builder_version=”4.17.3″ global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_divider _builder_version=”4.16″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_divider][et_pb_text admin_label=”Title” _builder_version=”4.17.3″ header_3_font=”Teko||||||||” header_3_font_size=”40px” header_3_line_height=”1.2em” vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ text_orientation=”center” custom_margin=”||15px|” z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
How to be Proactive Against Ransomware Attacks
[/et_pb_text][/et_pb_column][/et_pb_row][et_pb_row column_structure=”1_3,1_3,1_3″ module_id=”anchor-top” _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][et_pb_column type=”1_3″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_image src=”https://itcstpete.com/wp-content/uploads/2022/05/Pen-Testing-Icons-1.png” url=”#anchor-1″ align=”center” module_id=”#anchor-1″ _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_image][et_pb_text _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Penetration Testing
[/et_pb_text][/et_pb_column][et_pb_column type=”1_3″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_image src=”https://itcstpete.com/wp-content/uploads/2022/05/Encryption-Icons-1.png” url=”#anchor-2″ align=”center” module_id=”#anchor-2″ _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_image][et_pb_text _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Encryption
[/et_pb_text][/et_pb_column][et_pb_column type=”1_3″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_image src=”https://itcstpete.com/wp-content/uploads/2022/05/CCaaS-Icons-1.png” url=”#anchor-3″ align=”center” module_id=”#anchor-3″ _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_image][et_pb_text _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
CSaaS
[/et_pb_text][/et_pb_column][/et_pb_row][et_pb_row _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_divider _builder_version=”4.16″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_divider][et_pb_text admin_label=”Title” _builder_version=”4.17.3″ header_3_font=”Teko||||||||” header_3_font_size=”40px” header_3_line_height=”1.2em” vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_margin=”||15px|” z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Already been a victim of an Ransomware Attack?
[/et_pb_text][/et_pb_column][/et_pb_row][et_pb_row column_structure=”1_3,1_3,1_3″ _builder_version=”4.16″ background_size=”initial” background_position=”top_left” background_repeat=”repeat” global_colors_info=”{}”][et_pb_column type=”1_3″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_image src=”https://itcstpete.com/wp-content/uploads/2022/05/DarkWeb-Icons-1.png” url=”#anchor-4″ align=”center” module_id=”#anchor-1″ _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_image][et_pb_text _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Dark Web Scanning
[/et_pb_text][/et_pb_column][et_pb_column type=”1_3″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_image src=”https://itcstpete.com/wp-content/uploads/2022/05/IR-Icons-1.png” url=”#anchor-5″ align=”center” module_id=”#anchor-2″ _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_image][et_pb_text _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Incident Response
[/et_pb_text][/et_pb_column][et_pb_column type=”1_3″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_image src=”https://itcstpete.com/wp-content/uploads/2022/05/Remediation-Icons-1.png” url=”#anchor-6″ align=”center” module_id=”#anchor-3″ _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_image][et_pb_text _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Remediations
[/et_pb_text][/et_pb_column][/et_pb_row][et_pb_row _builder_version=”4.16″ background_size=”initial” background_position=”top_left” background_repeat=”repeat” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_divider _builder_version=”4.16″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_divider][/et_pb_column][/et_pb_row][et_pb_row column_structure=”1_2,1_2″ module_id=”anchor-1″ _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][et_pb_column type=”1_2″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_text admin_label=”Pen Testing” module_id=”#anchor-1″ _builder_version=”4.17.3″ header_3_font=”Teko||||||||” header_3_font_size=”40px” header_3_line_height=”1.2em” vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_margin=”||15px|” z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Penetration Testing
[/et_pb_text][et_pb_text _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
There are many ways to perform a Pen Test. It is essentially a team of well trained white hat hackers that will push the limits as far as you allow to try and get into your business. See some of the options below.
EXTERNAL ASSESSMENT
Securing the perimeter of your network is essential in ensuring that your network can withstand blows from malicious attackers. External Penetration Testing or “hacking from the internet” identifies what malicious attackers can find, see, exploit, and how far an attacker can penetrate once a network foothold is gained.
INTERNAL ASSESSMENT
Most networks are like candy, hard on the outside but soft and gooey on the inside. Security conscious professionals know that having a hardened interior network is just as important as having a hardened perimeter. Internal Penetration Testing assesses the security from the point of view of a corporate bad seed, disgruntled employee, or an attacker who has breached the perimeter through other means.
[/et_pb_text][et_pb_button button_url=”https://itcstpete.com/contact/” button_text=”Contact An Expert” button_alignment=”center” _builder_version=”4.16″ custom_button=”on” button_text_size=”16px” button_bg_color=”#c10f1b” button_border_width=”8px” button_border_color=”#c10f1b” button_border_radius=”0px” button_letter_spacing=”4px” button_font=”Teko|700||on|||||” button_icon=”$||divi||400″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ background_layout=”dark” z_index_tablet=”0″ button_text_shadow_horizontal_length_tablet=”0px” button_text_shadow_vertical_length_tablet=”0px” button_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}” button_text_size__hover_enabled=”off” button_text_size__hover=”null” button_one_text_size__hover_enabled=”off” button_one_text_size__hover=”null” button_two_text_size__hover_enabled=”off” button_two_text_size__hover=”null” button_text_color__hover_enabled=”off” button_text_color__hover=”null” button_one_text_color__hover_enabled=”off” button_one_text_color__hover=”null” button_two_text_color__hover_enabled=”off” button_two_text_color__hover=”null” button_border_width__hover_enabled=”off” button_border_width__hover=”null” button_one_border_width__hover_enabled=”off” button_one_border_width__hover=”null” button_two_border_width__hover_enabled=”off” button_two_border_width__hover=”null” button_border_color__hover_enabled=”off” button_border_color__hover=”null” button_one_border_color__hover_enabled=”off” button_one_border_color__hover=”null” button_two_border_color__hover_enabled=”off” button_two_border_color__hover=”null” button_border_radius__hover_enabled=”off” button_border_radius__hover=”null” button_one_border_radius__hover_enabled=”off” button_one_border_radius__hover=”null” button_two_border_radius__hover_enabled=”off” button_two_border_radius__hover=”null” button_letter_spacing__hover_enabled=”off” button_letter_spacing__hover=”null” button_one_letter_spacing__hover_enabled=”off” button_one_letter_spacing__hover=”null” button_two_letter_spacing__hover_enabled=”off” button_two_letter_spacing__hover=”null” button_bg_color__hover_enabled=”off” button_bg_color__hover=”null” button_one_bg_color__hover_enabled=”off” button_one_bg_color__hover=”null” button_two_bg_color__hover_enabled=”off” button_two_bg_color__hover=”null”][/et_pb_button][/et_pb_column][et_pb_column type=”1_2″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_image src=”https://itcstpete.com/wp-content/uploads/2022/02/penetration-testing-image-.jpg” _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_margin=”75px|||” z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_image][et_pb_text _builder_version=”4.16″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
WIRELESS SECURITY ASSESSMENT
WiFi in corporate settings has been increasing in popularity over the last decade. With weak WiFi security controls, an attacker could breach the perimeter of your network and access critical data, putting your company in the security breach hot seat. A Wireless Penetration Test will identify what mechanisms are in place to protect your wireless network and identify the current controls are sufficient in preventing unauthorized access to your network and data.
ANALOG SECURITY ASSESSMENT
The analog assessment or “War Dial” is conducted to test the security of all devices with an analog connection such as telephones and modems. The organization’s entire range of telephone numbers are dialed and tested for known security vulnerabilities.
[/et_pb_text][/et_pb_column][/et_pb_row][et_pb_row _builder_version=”4.16″ background_size=”initial” background_position=”top_left” background_repeat=”repeat” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_blurb url=”#anchor-top” use_icon=”on” font_icon=”%%21%%” icon_color=”#bf7a7a” image_icon_width=”40px” image_icon_width_tablet=”101px” admin_label=”Top” _builder_version=”4.16″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ link_option_url=”#anchor-top” z_index_tablet=”0″ header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” body_text_shadow_horizontal_length_tablet=”0px” body_text_shadow_vertical_length_tablet=”0px” body_text_shadow_blur_strength_tablet=”1px” body_link_text_shadow_horizontal_length_tablet=”0px” body_link_text_shadow_vertical_length_tablet=”0px” body_link_text_shadow_blur_strength_tablet=”1px” body_ul_text_shadow_horizontal_length_tablet=”0px” body_ul_text_shadow_vertical_length_tablet=”0px” body_ul_text_shadow_blur_strength_tablet=”1px” body_ol_text_shadow_horizontal_length_tablet=”0px” body_ol_text_shadow_vertical_length_tablet=”0px” body_ol_text_shadow_blur_strength_tablet=”1px” body_quote_text_shadow_horizontal_length_tablet=”0px” body_quote_text_shadow_vertical_length_tablet=”0px” body_quote_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” box_shadow_horizontal_image_tablet=”0px” box_shadow_vertical_image_tablet=”0px” box_shadow_blur_image_tablet=”40px” box_shadow_spread_image_tablet=”0px” text_shadow_horizontal_length_tablet=”0px” text_shadow_vertical_length_tablet=”0px” text_shadow_blur_strength_tablet=”1px” global_colors_info=”{}”][/et_pb_blurb][et_pb_divider _builder_version=”4.16″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_divider][/et_pb_column][/et_pb_row][et_pb_row column_structure=”1_2,1_2″ module_id=”anchor-2″ _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][et_pb_column type=”1_2″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_text admin_label=”Encryption” _builder_version=”4.17.3″ header_3_font=”Teko||||||||” header_3_font_size=”40px” header_3_line_height=”1.2em” vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_margin=”||15px|” z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Encryption
[/et_pb_text][et_pb_text _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Encryption enhances the security by scrambling or encrypting data that can only be unlocked with a specific key or code. To encrypt the data, you need the right key, and you need the right key to decrypt it as well. It is the most effective way to hide communication via encoded information where the sender and the recipient hold the key to decipher data.
Our partners have a simplified database encryption by providing a single integrated key management and hardware security module (HSM) to manage and store cryptographic keys across all your databases.
Stringent data privacy regulations, the risk of data breaches, and the migration of databases to the public cloud are driving many organizations to implement database encryption. And even though most databases offer integrated encryption capabilities, your data may still be susceptible to a breach unless there is proper key storage, policy management and auditing. Fortanix provides an integrated key management and hardware security module (HSM) solution designed to support database encryption across multiple datacenter sites, public cloud, and database vendors.
[/et_pb_text][/et_pb_column][et_pb_column type=”1_2″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_image src=”https://itcstpete.com/wp-content/uploads/2022/05/encryption-keys-lock-digital-concept.jpg” _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_margin=”75px|||” z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_image][et_pb_button button_url=”https://itcstpete.com/contact/” button_text=”Contact An Expert” button_alignment=”center” _builder_version=”4.16″ custom_button=”on” button_text_size=”16px” button_bg_color=”#c10f1b” button_border_width=”8px” button_border_color=”#c10f1b” button_border_radius=”0px” button_letter_spacing=”4px” button_font=”Teko|700||on|||||” button_icon=”$||divi||400″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ background_layout=”dark” z_index_tablet=”0″ button_text_shadow_horizontal_length_tablet=”0px” button_text_shadow_vertical_length_tablet=”0px” button_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}” button_text_size__hover_enabled=”off” button_text_size__hover=”null” button_one_text_size__hover_enabled=”off” button_one_text_size__hover=”null” button_two_text_size__hover_enabled=”off” button_two_text_size__hover=”null” button_text_color__hover_enabled=”off” button_text_color__hover=”null” button_one_text_color__hover_enabled=”off” button_one_text_color__hover=”null” button_two_text_color__hover_enabled=”off” button_two_text_color__hover=”null” button_border_width__hover_enabled=”off” button_border_width__hover=”null” button_one_border_width__hover_enabled=”off” button_one_border_width__hover=”null” button_two_border_width__hover_enabled=”off” button_two_border_width__hover=”null” button_border_color__hover_enabled=”off” button_border_color__hover=”null” button_one_border_color__hover_enabled=”off” button_one_border_color__hover=”null” button_two_border_color__hover_enabled=”off” button_two_border_color__hover=”null” button_border_radius__hover_enabled=”off” button_border_radius__hover=”null” button_one_border_radius__hover_enabled=”off” button_one_border_radius__hover=”null” button_two_border_radius__hover_enabled=”off” button_two_border_radius__hover=”null” button_letter_spacing__hover_enabled=”off” button_letter_spacing__hover=”null” button_one_letter_spacing__hover_enabled=”off” button_one_letter_spacing__hover=”null” button_two_letter_spacing__hover_enabled=”off” button_two_letter_spacing__hover=”null” button_bg_color__hover_enabled=”off” button_bg_color__hover=”null” button_one_bg_color__hover_enabled=”off” button_one_bg_color__hover=”null” button_two_bg_color__hover_enabled=”off” button_two_bg_color__hover=”null”][/et_pb_button][/et_pb_column][/et_pb_row][et_pb_row _builder_version=”4.16″ background_size=”initial” background_position=”top_left” background_repeat=”repeat” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_blurb url=”#anchor-top” use_icon=”on” font_icon=”%%21%%” icon_color=”#bf7a7a” image_icon_width=”40px” image_icon_width_tablet=”101px” admin_label=”Top” _builder_version=”4.16″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ link_option_url=”#anchor-top” z_index_tablet=”0″ header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” body_text_shadow_horizontal_length_tablet=”0px” body_text_shadow_vertical_length_tablet=”0px” body_text_shadow_blur_strength_tablet=”1px” body_link_text_shadow_horizontal_length_tablet=”0px” body_link_text_shadow_vertical_length_tablet=”0px” body_link_text_shadow_blur_strength_tablet=”1px” body_ul_text_shadow_horizontal_length_tablet=”0px” body_ul_text_shadow_vertical_length_tablet=”0px” body_ul_text_shadow_blur_strength_tablet=”1px” body_ol_text_shadow_horizontal_length_tablet=”0px” body_ol_text_shadow_vertical_length_tablet=”0px” body_ol_text_shadow_blur_strength_tablet=”1px” body_quote_text_shadow_horizontal_length_tablet=”0px” body_quote_text_shadow_vertical_length_tablet=”0px” body_quote_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” box_shadow_horizontal_image_tablet=”0px” box_shadow_vertical_image_tablet=”0px” box_shadow_blur_image_tablet=”40px” box_shadow_spread_image_tablet=”0px” text_shadow_horizontal_length_tablet=”0px” text_shadow_vertical_length_tablet=”0px” text_shadow_blur_strength_tablet=”1px” global_colors_info=”{}”][/et_pb_blurb][et_pb_divider _builder_version=”4.16″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_divider][/et_pb_column][/et_pb_row][et_pb_row column_structure=”1_2,1_2″ module_id=”anchor-3″ _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][et_pb_column type=”1_2″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_text admin_label=”CSaaS” _builder_version=”4.17.3″ header_3_font=”Teko||||||||” header_3_font_size=”40px” header_3_line_height=”1.2em” vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_margin=”||15px|” z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Cyber Security As A Service (CSaaS)
[/et_pb_text][et_pb_text _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Our Good cybersecurity isn’t a one-time event. It’s an ongoing, continuous process. And that’s exactly what Cybersecurity as a Service (CSaaS) delivers. As a subscription-based cybersecurity solution, CSaaS allows every business to have access to the most secure options available. No longer do you have to be in the Fortune 500 to get access to:
- Expert cybersecurity practitioners
- Security solutions that make sense for your unique organization
- Efficient remediation for any issues that arise
- Effective ROI tracking on all of your investments
With Cybersecurity as a Service, you’ll no longer have to manage your security internally or hope for the best from fair-weather providers. Your cybersecurity will be effortless regardless of the type or size of your business with CSaaS.
[/et_pb_text][/et_pb_column][et_pb_column type=”1_2″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_video src=”https://youtu.be/otIoh_mM_Mk?si=lVwzmXwm7XORFt5V” _builder_version=”4.17.1″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_margin=”100px|||” z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_video][et_pb_button button_url=”https://itcstpete.com/contact/” button_text=”Contact An Expert” button_alignment=”center” _builder_version=”4.16″ custom_button=”on” button_text_size=”16px” button_bg_color=”#c10f1b” button_border_width=”8px” button_border_color=”#c10f1b” button_border_radius=”0px” button_letter_spacing=”4px” button_font=”Teko|700||on|||||” button_icon=”$||divi||400″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ background_layout=”dark” z_index_tablet=”0″ button_text_shadow_horizontal_length_tablet=”0px” button_text_shadow_vertical_length_tablet=”0px” button_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}” button_text_size__hover_enabled=”off” button_text_size__hover=”null” button_one_text_size__hover_enabled=”off” button_one_text_size__hover=”null” button_two_text_size__hover_enabled=”off” button_two_text_size__hover=”null” button_text_color__hover_enabled=”off” button_text_color__hover=”null” button_one_text_color__hover_enabled=”off” button_one_text_color__hover=”null” button_two_text_color__hover_enabled=”off” button_two_text_color__hover=”null” button_border_width__hover_enabled=”off” button_border_width__hover=”null” button_one_border_width__hover_enabled=”off” button_one_border_width__hover=”null” button_two_border_width__hover_enabled=”off” button_two_border_width__hover=”null” button_border_color__hover_enabled=”off” button_border_color__hover=”null” button_one_border_color__hover_enabled=”off” button_one_border_color__hover=”null” button_two_border_color__hover_enabled=”off” button_two_border_color__hover=”null” button_border_radius__hover_enabled=”off” button_border_radius__hover=”null” button_one_border_radius__hover_enabled=”off” button_one_border_radius__hover=”null” button_two_border_radius__hover_enabled=”off” button_two_border_radius__hover=”null” button_letter_spacing__hover_enabled=”off” button_letter_spacing__hover=”null” button_one_letter_spacing__hover_enabled=”off” button_one_letter_spacing__hover=”null” button_two_letter_spacing__hover_enabled=”off” button_two_letter_spacing__hover=”null” button_bg_color__hover_enabled=”off” button_bg_color__hover=”null” button_one_bg_color__hover_enabled=”off” button_one_bg_color__hover=”null” button_two_bg_color__hover_enabled=”off” button_two_bg_color__hover=”null”][/et_pb_button][/et_pb_column][/et_pb_row][et_pb_row _builder_version=”4.16″ background_size=”initial” background_position=”top_left” background_repeat=”repeat” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_blurb url=”#anchor-top” use_icon=”on” font_icon=”%%21%%” icon_color=”#bf7a7a” image_icon_width=”40px” image_icon_width_tablet=”101px” admin_label=”Top” _builder_version=”4.16″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ link_option_url=”#anchor-top” z_index_tablet=”0″ header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” body_text_shadow_horizontal_length_tablet=”0px” body_text_shadow_vertical_length_tablet=”0px” body_text_shadow_blur_strength_tablet=”1px” body_link_text_shadow_horizontal_length_tablet=”0px” body_link_text_shadow_vertical_length_tablet=”0px” body_link_text_shadow_blur_strength_tablet=”1px” body_ul_text_shadow_horizontal_length_tablet=”0px” body_ul_text_shadow_vertical_length_tablet=”0px” body_ul_text_shadow_blur_strength_tablet=”1px” body_ol_text_shadow_horizontal_length_tablet=”0px” body_ol_text_shadow_vertical_length_tablet=”0px” body_ol_text_shadow_blur_strength_tablet=”1px” body_quote_text_shadow_horizontal_length_tablet=”0px” body_quote_text_shadow_vertical_length_tablet=”0px” body_quote_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” box_shadow_horizontal_image_tablet=”0px” box_shadow_vertical_image_tablet=”0px” box_shadow_blur_image_tablet=”40px” box_shadow_spread_image_tablet=”0px” text_shadow_horizontal_length_tablet=”0px” text_shadow_vertical_length_tablet=”0px” text_shadow_blur_strength_tablet=”1px” global_colors_info=”{}”][/et_pb_blurb][et_pb_divider _builder_version=”4.16″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_divider][/et_pb_column][/et_pb_row][et_pb_row column_structure=”1_2,1_2″ module_id=”anchor-4″ _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][et_pb_column type=”1_2″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_text admin_label=”Dark Web Scanning” _builder_version=”4.17.3″ header_3_font=”Teko||||||||” header_3_font_size=”40px” header_3_line_height=”1.2em” vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_margin=”||15px|” z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Dark Web Scanning
[/et_pb_text][et_pb_text _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Dark Web Scanning is a service we offer that will search the dark web for you, tediously looking through its vast databases of stolen usernames, passwords, Social Security numbers, and credit card numbers for sale.
If your info is found in any form from these scans, we will then notify you and provide with what we found. Unfortunately, in most cases, there is usually no way of actually removing your information from the dark web, but once we know what information has been compromised, we can help you protect your business against another attack or any other information getting hacked again.
[/et_pb_text][/et_pb_column][et_pb_column type=”1_2″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_image src=”https://itcstpete.com/wp-content/uploads/2022/05/dark-web-scanning-.png” _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_margin=”75px|||” z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_image][et_pb_button button_url=”https://itcstpete.com/contact/” button_text=”Contact An Expert” button_alignment=”center” _builder_version=”4.16″ custom_button=”on” button_text_size=”16px” button_bg_color=”#c10f1b” button_border_width=”8px” button_border_color=”#c10f1b” button_border_radius=”0px” button_letter_spacing=”4px” button_font=”Teko|700||on|||||” button_icon=”$||divi||400″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ background_layout=”dark” z_index_tablet=”0″ button_text_shadow_horizontal_length_tablet=”0px” button_text_shadow_vertical_length_tablet=”0px” button_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}” button_text_size__hover_enabled=”off” button_text_size__hover=”null” button_one_text_size__hover_enabled=”off” button_one_text_size__hover=”null” button_two_text_size__hover_enabled=”off” button_two_text_size__hover=”null” button_text_color__hover_enabled=”off” button_text_color__hover=”null” button_one_text_color__hover_enabled=”off” button_one_text_color__hover=”null” button_two_text_color__hover_enabled=”off” button_two_text_color__hover=”null” button_border_width__hover_enabled=”off” button_border_width__hover=”null” button_one_border_width__hover_enabled=”off” button_one_border_width__hover=”null” button_two_border_width__hover_enabled=”off” button_two_border_width__hover=”null” button_border_color__hover_enabled=”off” button_border_color__hover=”null” button_one_border_color__hover_enabled=”off” button_one_border_color__hover=”null” button_two_border_color__hover_enabled=”off” button_two_border_color__hover=”null” button_border_radius__hover_enabled=”off” button_border_radius__hover=”null” button_one_border_radius__hover_enabled=”off” button_one_border_radius__hover=”null” button_two_border_radius__hover_enabled=”off” button_two_border_radius__hover=”null” button_letter_spacing__hover_enabled=”off” button_letter_spacing__hover=”null” button_one_letter_spacing__hover_enabled=”off” button_one_letter_spacing__hover=”null” button_two_letter_spacing__hover_enabled=”off” button_two_letter_spacing__hover=”null” button_bg_color__hover_enabled=”off” button_bg_color__hover=”null” button_one_bg_color__hover_enabled=”off” button_one_bg_color__hover=”null” button_two_bg_color__hover_enabled=”off” button_two_bg_color__hover=”null”][/et_pb_button][/et_pb_column][/et_pb_row][et_pb_row _builder_version=”4.16″ background_size=”initial” background_position=”top_left” background_repeat=”repeat” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_blurb url=”#anchor-top” use_icon=”on” font_icon=”%%21%%” icon_color=”#bf7a7a” image_icon_width=”40px” image_icon_width_tablet=”101px” admin_label=”Top” _builder_version=”4.16″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ link_option_url=”#anchor-top” z_index_tablet=”0″ header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” body_text_shadow_horizontal_length_tablet=”0px” body_text_shadow_vertical_length_tablet=”0px” body_text_shadow_blur_strength_tablet=”1px” body_link_text_shadow_horizontal_length_tablet=”0px” body_link_text_shadow_vertical_length_tablet=”0px” body_link_text_shadow_blur_strength_tablet=”1px” body_ul_text_shadow_horizontal_length_tablet=”0px” body_ul_text_shadow_vertical_length_tablet=”0px” body_ul_text_shadow_blur_strength_tablet=”1px” body_ol_text_shadow_horizontal_length_tablet=”0px” body_ol_text_shadow_vertical_length_tablet=”0px” body_ol_text_shadow_blur_strength_tablet=”1px” body_quote_text_shadow_horizontal_length_tablet=”0px” body_quote_text_shadow_vertical_length_tablet=”0px” body_quote_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” box_shadow_horizontal_image_tablet=”0px” box_shadow_vertical_image_tablet=”0px” box_shadow_blur_image_tablet=”40px” box_shadow_spread_image_tablet=”0px” text_shadow_horizontal_length_tablet=”0px” text_shadow_vertical_length_tablet=”0px” text_shadow_blur_strength_tablet=”1px” global_colors_info=”{}”][/et_pb_blurb][et_pb_divider _builder_version=”4.16″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_divider][/et_pb_column][/et_pb_row][et_pb_row column_structure=”1_2,1_2″ module_id=”anchor-5″ _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][et_pb_column type=”1_2″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_text admin_label=”Incident Response” _builder_version=”4.17.3″ header_3_font=”Teko||||||||” header_3_font_size=”40px” header_3_line_height=”1.2em” vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_margin=”||15px|” z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
24/7 Incident Response Team
[/et_pb_text][et_pb_text _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
INCIDENT RESPONSE
We are partnered with a company that has the experience and expertise required to properly manage and respond to a security breach. Incident response is a unique field of information security and risk management that focuses on managing data loss and maintaining business continuity following a security breach or incident.
Our partner, Secure Network’s, staff will work with you to identify the nature and extent of the incident at hand. The idea is to build an effective mitigation strategy as quickly as possible, covering the entire range of the breach. Secure Network takes a tactical approach to every incident response case. We then work with the client to provide strategic risk mitigation guidance to prevent future incidents.
[/et_pb_text][/et_pb_column][et_pb_column type=”1_2″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_image src=”https://itcstpete.com/wp-content/uploads/2022/05/incidentResponse.webp” _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_margin=”75px|||” z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_image][et_pb_button button_url=”https://itcstpete.com/contact/” button_text=”Contact An Expert” button_alignment=”center” _builder_version=”4.16″ custom_button=”on” button_text_size=”16px” button_bg_color=”#c10f1b” button_border_width=”8px” button_border_color=”#c10f1b” button_border_radius=”0px” button_letter_spacing=”4px” button_font=”Teko|700||on|||||” button_icon=”$||divi||400″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ background_layout=”dark” z_index_tablet=”0″ button_text_shadow_horizontal_length_tablet=”0px” button_text_shadow_vertical_length_tablet=”0px” button_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}” button_text_size__hover_enabled=”off” button_text_size__hover=”null” button_one_text_size__hover_enabled=”off” button_one_text_size__hover=”null” button_two_text_size__hover_enabled=”off” button_two_text_size__hover=”null” button_text_color__hover_enabled=”off” button_text_color__hover=”null” button_one_text_color__hover_enabled=”off” button_one_text_color__hover=”null” button_two_text_color__hover_enabled=”off” button_two_text_color__hover=”null” button_border_width__hover_enabled=”off” button_border_width__hover=”null” button_one_border_width__hover_enabled=”off” button_one_border_width__hover=”null” button_two_border_width__hover_enabled=”off” button_two_border_width__hover=”null” button_border_color__hover_enabled=”off” button_border_color__hover=”null” button_one_border_color__hover_enabled=”off” button_one_border_color__hover=”null” button_two_border_color__hover_enabled=”off” button_two_border_color__hover=”null” button_border_radius__hover_enabled=”off” button_border_radius__hover=”null” button_one_border_radius__hover_enabled=”off” button_one_border_radius__hover=”null” button_two_border_radius__hover_enabled=”off” button_two_border_radius__hover=”null” button_letter_spacing__hover_enabled=”off” button_letter_spacing__hover=”null” button_one_letter_spacing__hover_enabled=”off” button_one_letter_spacing__hover=”null” button_two_letter_spacing__hover_enabled=”off” button_two_letter_spacing__hover=”null” button_bg_color__hover_enabled=”off” button_bg_color__hover=”null” button_one_bg_color__hover_enabled=”off” button_one_bg_color__hover=”null” button_two_bg_color__hover_enabled=”off” button_two_bg_color__hover=”null”][/et_pb_button][/et_pb_column][/et_pb_row][et_pb_row _builder_version=”4.16″ background_size=”initial” background_position=”top_left” background_repeat=”repeat” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_blurb url=”#anchor-top” use_icon=”on” font_icon=”%%21%%” icon_color=”#bf7a7a” image_icon_width=”40px” image_icon_width_tablet=”101px” admin_label=”Top” _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ link_option_url=”#anchor-top” z_index_tablet=”0″ header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” body_text_shadow_horizontal_length_tablet=”0px” body_text_shadow_vertical_length_tablet=”0px” body_text_shadow_blur_strength_tablet=”1px” body_link_text_shadow_horizontal_length_tablet=”0px” body_link_text_shadow_vertical_length_tablet=”0px” body_link_text_shadow_blur_strength_tablet=”1px” body_ul_text_shadow_horizontal_length_tablet=”0px” body_ul_text_shadow_vertical_length_tablet=”0px” body_ul_text_shadow_blur_strength_tablet=”1px” body_ol_text_shadow_horizontal_length_tablet=”0px” body_ol_text_shadow_vertical_length_tablet=”0px” body_ol_text_shadow_blur_strength_tablet=”1px” body_quote_text_shadow_horizontal_length_tablet=”0px” body_quote_text_shadow_vertical_length_tablet=”0px” body_quote_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” box_shadow_horizontal_image_tablet=”0px” box_shadow_vertical_image_tablet=”0px” box_shadow_blur_image_tablet=”40px” box_shadow_spread_image_tablet=”0px” text_shadow_horizontal_length_tablet=”0px” text_shadow_vertical_length_tablet=”0px” text_shadow_blur_strength_tablet=”1px” global_colors_info=”{}”][/et_pb_blurb][et_pb_divider _builder_version=”4.16″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_divider][/et_pb_column][/et_pb_row][et_pb_row column_structure=”1_2,1_2″ module_id=”anchor-6″ _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][et_pb_column type=”1_2″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_text admin_label=”Remediations” _builder_version=”4.17.3″ header_3_font=”Teko||||||||” header_3_font_size=”40px” header_3_line_height=”1.2em” vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_margin=”||15px|” z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Remediations
[/et_pb_text][et_pb_text _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”]
Whether you have already been hit with a ransomware attack or if you just want to improve your security posture, we can provide you with options on what solutions or changes would best suit your business. Utilizing services like Penetration Testing and CSaaS will allow us to see your vulnerabilities and remediate them. Remediations can cover everything from new hardware and software depending on your budget and needs.
[/et_pb_text][/et_pb_column][et_pb_column type=”1_2″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_image src=”https://itcstpete.com/wp-content/uploads/2022/02/incident-response.jpg” _builder_version=”4.17.3″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ custom_margin=”75px|||” z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_image][et_pb_button button_url=”https://itcstpete.com/contact/” button_text=”Contact An Expert” button_alignment=”center” _builder_version=”4.16″ custom_button=”on” button_text_size=”16px” button_bg_color=”#c10f1b” button_border_width=”8px” button_border_color=”#c10f1b” button_border_radius=”0px” button_letter_spacing=”4px” button_font=”Teko|700||on|||||” button_icon=”$||divi||400″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ background_layout=”dark” z_index_tablet=”0″ button_text_shadow_horizontal_length_tablet=”0px” button_text_shadow_vertical_length_tablet=”0px” button_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}” button_text_size__hover_enabled=”off” button_text_size__hover=”null” button_one_text_size__hover_enabled=”off” button_one_text_size__hover=”null” button_two_text_size__hover_enabled=”off” button_two_text_size__hover=”null” button_text_color__hover_enabled=”off” button_text_color__hover=”null” button_one_text_color__hover_enabled=”off” button_one_text_color__hover=”null” button_two_text_color__hover_enabled=”off” button_two_text_color__hover=”null” button_border_width__hover_enabled=”off” button_border_width__hover=”null” button_one_border_width__hover_enabled=”off” button_one_border_width__hover=”null” button_two_border_width__hover_enabled=”off” button_two_border_width__hover=”null” button_border_color__hover_enabled=”off” button_border_color__hover=”null” button_one_border_color__hover_enabled=”off” button_one_border_color__hover=”null” button_two_border_color__hover_enabled=”off” button_two_border_color__hover=”null” button_border_radius__hover_enabled=”off” button_border_radius__hover=”null” button_one_border_radius__hover_enabled=”off” button_one_border_radius__hover=”null” button_two_border_radius__hover_enabled=”off” button_two_border_radius__hover=”null” button_letter_spacing__hover_enabled=”off” button_letter_spacing__hover=”null” button_one_letter_spacing__hover_enabled=”off” button_one_letter_spacing__hover=”null” button_two_letter_spacing__hover_enabled=”off” button_two_letter_spacing__hover=”null” button_bg_color__hover_enabled=”off” button_bg_color__hover=”null” button_one_bg_color__hover_enabled=”off” button_one_bg_color__hover=”null” button_two_bg_color__hover_enabled=”off” button_two_bg_color__hover=”null”][/et_pb_button][/et_pb_column][/et_pb_row][et_pb_row _builder_version=”4.16″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_blurb url=”#anchor-top” use_icon=”on” font_icon=”%%21%%” icon_color=”#bf7a7a” image_icon_width=”40px” image_icon_width_tablet=”101px” admin_label=”Top” _builder_version=”4.16″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ link_option_url=”#anchor-top” z_index_tablet=”0″ header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” body_text_shadow_horizontal_length_tablet=”0px” body_text_shadow_vertical_length_tablet=”0px” body_text_shadow_blur_strength_tablet=”1px” body_link_text_shadow_horizontal_length_tablet=”0px” body_link_text_shadow_vertical_length_tablet=”0px” body_link_text_shadow_blur_strength_tablet=”1px” body_ul_text_shadow_horizontal_length_tablet=”0px” body_ul_text_shadow_vertical_length_tablet=”0px” body_ul_text_shadow_blur_strength_tablet=”1px” body_ol_text_shadow_horizontal_length_tablet=”0px” body_ol_text_shadow_vertical_length_tablet=”0px” body_ol_text_shadow_blur_strength_tablet=”1px” body_quote_text_shadow_horizontal_length_tablet=”0px” body_quote_text_shadow_vertical_length_tablet=”0px” body_quote_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” box_shadow_horizontal_image_tablet=”0px” box_shadow_vertical_image_tablet=”0px” box_shadow_blur_image_tablet=”40px” box_shadow_spread_image_tablet=”0px” text_shadow_horizontal_length_tablet=”0px” text_shadow_vertical_length_tablet=”0px” text_shadow_blur_strength_tablet=”1px” global_colors_info=”{}”][/et_pb_blurb][et_pb_divider _builder_version=”4.16″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” global_colors_info=”{}”][/et_pb_divider][/et_pb_column][/et_pb_row][/et_pb_section][et_pb_section fb_built=”1″ make_equal=”on” use_custom_gutter=”on” gutter_width=”1″ specialty=”on” next_background_color=”#ffffff” background_color_2=”#c10f1b” padding_top_1=”150px” padding_top_2=”150px” padding_right_1=”60px” padding_right_2=”10%” padding_bottom_1=”150px” padding_bottom_2=”150px” padding_left_1=”10%” padding_left_2=”60px” padding_top_bottom_link_1=”true” padding_top_bottom_link_2=”true” padding_1_tablet=”|0%||0%||true” padding_2_tablet=”40px|10%|100px|10%||true” padding_1_phone=”” padding_2_phone=”” padding_1_last_edited=”on|desktop” padding_2_last_edited=”on|desktop” admin_label=”Footer” module_class=” et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth et_pb_specialty_fullwidth” _builder_version=”4.16″ use_background_color_gradient=”on” background_color_gradient_stops=”rgba(24,30,36,0.9) 0%|rgba(213,26,39,0.69) 100%” background_color_gradient_overlays_image=”on” background_color_gradient_start=”rgba(24,30,36,0.9)” background_color_gradient_end=”rgba(213,26,39,0.69)” background_image=”https://itcstpete.com/wp-content/uploads/2019/02/IT-consulting-st-pete-1.jpg” inner_width=”100%” inner_width_tablet=”100%” inner_width_phone=”” inner_width_last_edited=”on|desktop” inner_max_width=”100%” inner_max_width_tablet=”100%” inner_max_width_phone=”” inner_max_width_last_edited=”on|desktop” custom_padding=”0px||0px||true” bottom_divider_style=”arrow” bottom_divider_arrangement=”above_content” animation_style=”slide” animation_direction=”bottom” animation_intensity_slide=”4%” animation_starting_opacity=”100%” box_shadow_style=”preset7″ box_shadow_horizontal=”0px” box_shadow_vertical=”80px” box_shadow_color=”#ffffff” make_fullwidth=”on” saved_tabs=”all” global_colors_info=”{}”][et_pb_column type=”1_2″ specialty_columns=”2″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_row_inner _builder_version=”4.16″ custom_padding=”0|0px|0|0px|true|false” global_colors_info=”{}”][et_pb_column_inner saved_specialty_column_type=”1_2″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_text _builder_version=”4.16″ text_font=”Lato||||||||” text_font_size=”22px” text_line_height=”1.8em” header_font=”||||||||” header_2_font=”Teko||||||||” header_2_font_size=”96px” background_layout=”dark” custom_margin=”|||” header_2_font_size_tablet=”66px” header_2_font_size_phone=”36px” header_2_font_size_last_edited=”on|phone” locked=”off” global_colors_info=”{}”]
Get In Touch
[/et_pb_text][et_pb_text _builder_version=”4.16″ text_font=”Teko|500|||||||” text_font_size=”40px” text_line_height=”2em” vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ background_layout=”dark” custom_margin=”|||” z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” locked=”off” global_colors_info=”{}”]
(833)-ITC-WiFi or (727)-335-3133
[/et_pb_text][/et_pb_column_inner][/et_pb_row_inner][et_pb_row_inner column_structure=”1_2,1_2″ use_custom_gutter=”on” gutter_width=”2″ _builder_version=”4.16″ global_colors_info=”{}”][et_pb_column_inner type=”1_2″ saved_specialty_column_type=”1_2″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_text _builder_version=”4.17.1″ text_font=”Lato||||||||” text_font_size=”18px” text_line_height=”1.8em” header_4_font=”Teko|500|||||||” header_4_font_size=”22px” vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ background_layout=”dark” custom_margin=”|||” z_index_tablet=”0″ text_text_shadow_horizontal_length_tablet=”0px” text_text_shadow_vertical_length_tablet=”0px” text_text_shadow_blur_strength_tablet=”1px” link_text_shadow_horizontal_length_tablet=”0px” link_text_shadow_vertical_length_tablet=”0px” link_text_shadow_blur_strength_tablet=”1px” ul_text_shadow_horizontal_length_tablet=”0px” ul_text_shadow_vertical_length_tablet=”0px” ul_text_shadow_blur_strength_tablet=”1px” ol_text_shadow_horizontal_length_tablet=”0px” ol_text_shadow_vertical_length_tablet=”0px” ol_text_shadow_blur_strength_tablet=”1px” quote_text_shadow_horizontal_length_tablet=”0px” quote_text_shadow_vertical_length_tablet=”0px” quote_text_shadow_blur_strength_tablet=”1px” header_text_shadow_horizontal_length_tablet=”0px” header_text_shadow_vertical_length_tablet=”0px” header_text_shadow_blur_strength_tablet=”1px” header_2_text_shadow_horizontal_length_tablet=”0px” header_2_text_shadow_vertical_length_tablet=”0px” header_2_text_shadow_blur_strength_tablet=”1px” header_3_text_shadow_horizontal_length_tablet=”0px” header_3_text_shadow_vertical_length_tablet=”0px” header_3_text_shadow_blur_strength_tablet=”1px” header_4_text_shadow_horizontal_length_tablet=”0px” header_4_text_shadow_vertical_length_tablet=”0px” header_4_text_shadow_blur_strength_tablet=”1px” header_5_text_shadow_horizontal_length_tablet=”0px” header_5_text_shadow_vertical_length_tablet=”0px” header_5_text_shadow_blur_strength_tablet=”1px” header_6_text_shadow_horizontal_length_tablet=”0px” header_6_text_shadow_vertical_length_tablet=”0px” header_6_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” locked=”off” global_colors_info=”{}”]
Location
2520 N McMullen Booth Rd.
Suite B202
Clearwater, FL 33716
[/et_pb_text][et_pb_text _builder_version=”4.16″ text_font=”Lato||||||||” text_font_size=”18px” text_line_height=”1.8em” header_4_font=”Teko|500|||||||” header_4_font_size=”22px” background_layout=”dark” custom_margin=”|||” locked=”off” global_colors_info=”{}”]
info@itcstpete.com
[/et_pb_text][/et_pb_column_inner][et_pb_column_inner type=”1_2″ saved_specialty_column_type=”1_2″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_text _builder_version=”4.16″ text_font=”Lato||||||||” text_font_size=”18px” text_line_height=”1.8em” header_4_font=”Teko|500|||||||” header_4_font_size=”22px” background_layout=”dark” custom_margin=”|||” locked=”off” global_colors_info=”{}”]
Available Every Day
Mon: 8am – 11pm
Tue: 8am – 11pm
Wed: 8am – 11pm
Thur: 8am – 11pm
Fri: 8am – 11pm
Sat: 8am – 11pm
Sun: 8am – 11pm
[/et_pb_text][/et_pb_column_inner][/et_pb_row_inner][/et_pb_column][et_pb_column type=”1_2″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_contact_form email=”info@itcstpete.com” title=”Send A Message” custom_message=”%%name%%||et_pb_line_break_holder||%%email%%||et_pb_line_break_holder||%%message%%” success_message=”Your message has been sent.” submit_button_text=”Send Message” module_id=”et_pb_contact_form_0″ _builder_version=”4.17.3″ form_field_background_color=”rgba(0,0,0,0.15)” form_field_text_color=”#ffffff” form_field_focus_background_color=”#ffffff” title_font=”Teko||||||||” title_text_color=”#ffffff” title_font_size=”40px” title_line_height=”1.2em” captcha_text_color=”#ffffff” form_field_font=”Lato||||||||” form_field_font_size=”16px” custom_button=”on” button_text_color=”#c10f1b” button_bg_color=”#ffffff” button_border_width=”8px” button_border_color=”#ffffff” button_border_radius=”0px” button_letter_spacing=”4px” button_font=”Teko|||on|||||” button_icon=”$||divi||400″ vertical_offset_tablet=”0″ horizontal_offset_tablet=”0″ z_index_tablet=”0″ title_text_shadow_horizontal_length_tablet=”0px” title_text_shadow_vertical_length_tablet=”0px” title_text_shadow_blur_strength_tablet=”1px” captcha_text_shadow_horizontal_length_tablet=”0px” captcha_text_shadow_vertical_length_tablet=”0px” captcha_text_shadow_blur_strength_tablet=”1px” form_field_text_shadow_horizontal_length_tablet=”0px” form_field_text_shadow_vertical_length_tablet=”0px” form_field_text_shadow_blur_strength_tablet=”1px” button_text_shadow_horizontal_length_tablet=”0px” button_text_shadow_vertical_length_tablet=”0px” button_text_shadow_blur_strength_tablet=”1px” box_shadow_horizontal_tablet=”0px” box_shadow_vertical_tablet=”0px” box_shadow_blur_tablet=”40px” box_shadow_spread_tablet=”0px” box_shadow_horizontal_button_tablet=”0px” box_shadow_vertical_button_tablet=”0px” box_shadow_blur_button_tablet=”40px” box_shadow_spread_button_tablet=”0px” text_shadow_horizontal_length_tablet=”0px” text_shadow_vertical_length_tablet=”0px” text_shadow_blur_strength_tablet=”1px” locked=”off” global_colors_info=”{}”][et_pb_contact_field field_id=”Name” field_title=”Name” fullwidth_field=”on” _builder_version=”4.16″ global_colors_info=”{}” button_text_size__hover_enabled=”off” button_one_text_size__hover_enabled=”off” button_two_text_size__hover_enabled=”off” button_text_color__hover_enabled=”off” button_one_text_color__hover_enabled=”off” button_two_text_color__hover_enabled=”off” button_border_width__hover_enabled=”off” button_one_border_width__hover_enabled=”off” button_two_border_width__hover_enabled=”off” button_border_color__hover_enabled=”off” button_one_border_color__hover_enabled=”off” button_two_border_color__hover_enabled=”off” button_border_radius__hover_enabled=”off” button_one_border_radius__hover_enabled=”off” button_two_border_radius__hover_enabled=”off” button_letter_spacing__hover_enabled=”off” button_one_letter_spacing__hover_enabled=”off” button_two_letter_spacing__hover_enabled=”off” button_bg_color__hover_enabled=”off” button_one_bg_color__hover_enabled=”off” button_two_bg_color__hover_enabled=”off”][/et_pb_contact_field][et_pb_contact_field field_id=”Email” field_title=”Email Address” field_type=”email” fullwidth_field=”on” _builder_version=”4.16″ global_colors_info=”{}” button_text_size__hover_enabled=”off” button_one_text_size__hover_enabled=”off” button_two_text_size__hover_enabled=”off” button_text_color__hover_enabled=”off” button_one_text_color__hover_enabled=”off” button_two_text_color__hover_enabled=”off” button_border_width__hover_enabled=”off” button_one_border_width__hover_enabled=”off” button_two_border_width__hover_enabled=”off” button_border_color__hover_enabled=”off” button_one_border_color__hover_enabled=”off” button_two_border_color__hover_enabled=”off” button_border_radius__hover_enabled=”off” button_one_border_radius__hover_enabled=”off” button_two_border_radius__hover_enabled=”off” button_letter_spacing__hover_enabled=”off” button_one_letter_spacing__hover_enabled=”off” button_two_letter_spacing__hover_enabled=”off” button_bg_color__hover_enabled=”off” button_one_bg_color__hover_enabled=”off” button_two_bg_color__hover_enabled=”off”][/et_pb_contact_field][et_pb_contact_field field_id=”Message” field_title=”Message” field_type=”text” fullwidth_field=”on” _builder_version=”4.16″ global_colors_info=”{}” button_text_size__hover_enabled=”off” button_one_text_size__hover_enabled=”off” button_two_text_size__hover_enabled=”off” button_text_color__hover_enabled=”off” button_one_text_color__hover_enabled=”off” button_two_text_color__hover_enabled=”off” button_border_width__hover_enabled=”off” button_one_border_width__hover_enabled=”off” button_two_border_width__hover_enabled=”off” button_border_color__hover_enabled=”off” button_one_border_color__hover_enabled=”off” button_two_border_color__hover_enabled=”off” button_border_radius__hover_enabled=”off” button_one_border_radius__hover_enabled=”off” button_two_border_radius__hover_enabled=”off” button_letter_spacing__hover_enabled=”off” button_one_letter_spacing__hover_enabled=”off” button_two_letter_spacing__hover_enabled=”off” button_bg_color__hover_enabled=”off” button_one_bg_color__hover_enabled=”off” button_two_bg_color__hover_enabled=”off”][/et_pb_contact_field][/et_pb_contact_form][/et_pb_column][/et_pb_section]
